In this post, I would like to discuss about AWS Networking, VPC and all the associated components. We will cover a lots of AWS services and create a VPC from scratch in the hands-on demo and video.
The following diagrams show the components that I am covering in this post and video.
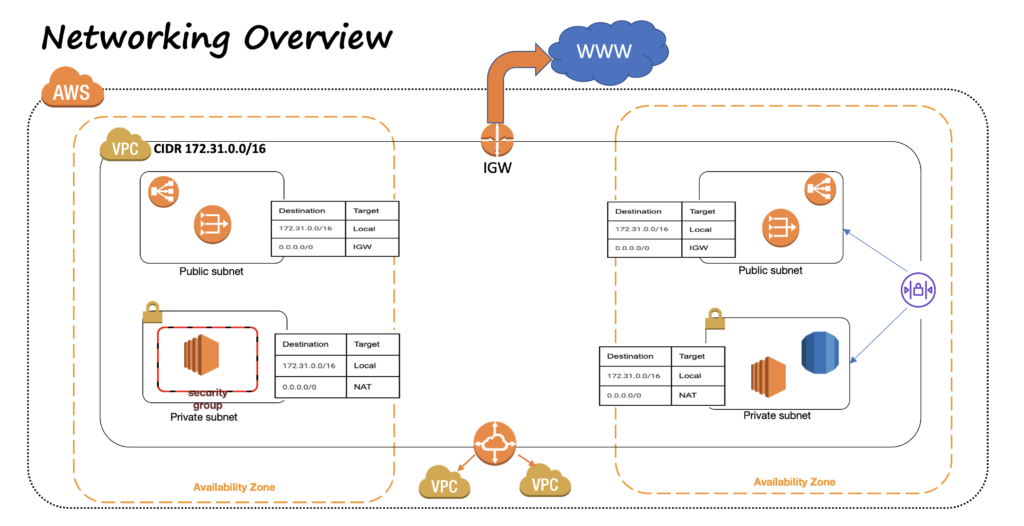
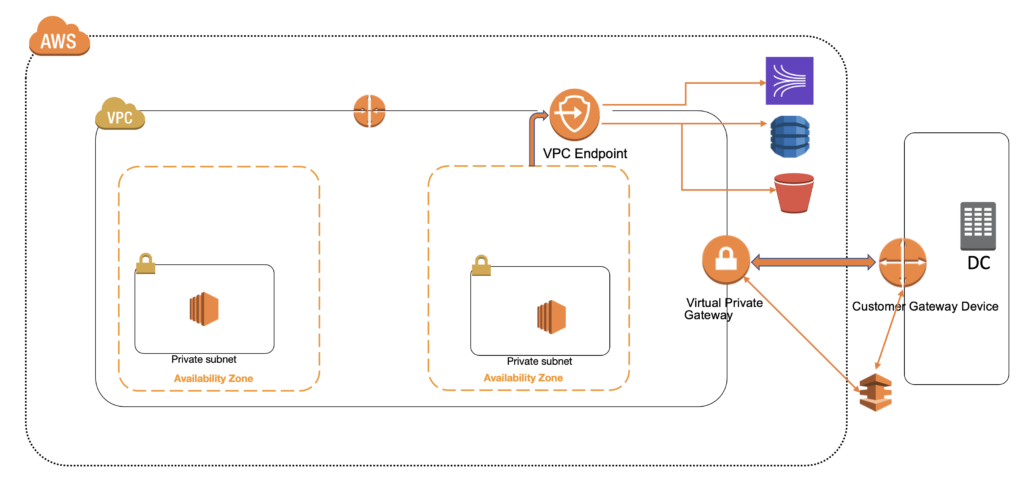
AWS Region And Availability Zones
A Region is a physical location around the world where AWS has their data centers. AWS maintains multiple geographical regions in North America, South America, Europe, Asia etc. Each AWS region consists of multiple isolated and physically separated Availability Zones. An Availability Zone is one or more discrete data centers with redundant power, cooling, physical security, networking and low latency connectivity.
AWS VPC
Amazon Virtual Private Cloud (Or VPC) is a service that lets you launch AWS resources in a logically isolated virtual network that you define. VPC is a regional resource. All AWS accounts when first created, have a DEFAULT VPC in every region. With VPC, we have complete control of our virtual networking environment, including IP Ranges, Subnets, route tables etc. There are several advantages of using Amazon VPC, like Secure and monitored network connections, it is logically isolated from other virtual networks in AWS cloud, customizable (in contrast to CLASS based IP ranges, where you get a fixed IP Address range based on Class you choose). When creating VPC, you need to specify CIDR range, for example, 10.0.0.0/16, which lets you create a network with 2^16 ip address.
Subnet
VPC spans across multiple availability zones. After creating VPC, we can add one or more subnets in each AZ. A sub-section of VPC’s IP range gets associated with the Subnet. There are 2 types of Subnets: Public and Private.
Resources like Load Balancers, Bastion hosts are deployed in Public Subnets.
Resources like Application Servers / EC2 instances, databases etc are created in Private Subnets.
The question is: What makes a subnet public or private?
Before we answer that, let’s talk about Internet Gateway. An Internet Gateway is a horizontally scaled, redundant and highly available VPC component that allows communication between the VPC and the Internet.
To enable Internet Access, we create an internet gateway and attach it to the VPC, add a route to the subnet’s route table that directs internet bound traffic to the InternetGateway.
Any Subnet, whose associated Route Table, has a route to the Internet Gateway, is Public Subnet. If the Subnet’s route table doesn’t have a route, is Private Subnet. It can only access the private resources within the VPC.
NAT Gateway
If you need the instances in your Private Subnet to connect to the Internet, for example to download security patches, or any other AWS services like S3 or DynamoDB etc, but at the same time prevent the Internet from initiating a connection with those instances, you can use NAT Gateway. NAT Gateways are created in Public Subnet(s) and have an Elastic Ip Address associated. After creating the NAT Gateway, you can modify the Route tables in the Private Subnets to point the Internet bound traffic to NAT Gateway.
Security Groups
A security group acts as a virtual firewall for instance to control inbound and outbound traffic. Security group act at an instance level not Subnet level. For example: You a web server, you can open the port 80 and 443 but block all other access from the outside, Or you can allow access to SSH from the IP address range of your corporate data center etc. The Security group rules are Stateful. If you allow incoming traffic on port 80, outgoing traffic is automatically allowed.
NACL
Network Access Control List (NACL) is an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets. This can provide additional layer of security. For example, if you have a database instance in a subnet, which you only want to be accessed by a Subnet where application servers are hosted. Rules in NACL are Stateless. An Inbound allow rule does not guarantee the same for oubound. You have to specify allow/deny rules in both directions.
VPC Peering
A VPC Peering connection is a network connection between two VPCs that enables you to route traffic between them. Instances in either VPC can communicate with each other as if they are on the same network. You can create VPC peering connection between your own VPC or with a VPC in another AWS account. VPC can be in different Regions as well. AWS uses the existing infrastructure of a VPC to create VPC peering connection. There is no single point of failure or bandwidth bottleneck.
Connecting to Corporate Data Center
By default instances in the Amazon VPC can not communicate with remote networks. There are 2 ways we can connect AWS VPC to Corporate Data Center:
- Site To Site VPN: This lets you establish a VPN tunnel between AWS VPC and Onsite network and supports Internet Protocol Security (IPSec) VPN connections. You create a Customer Gateway Device, which is a physical device or application on the Datacenter and Customer Gateway, which is an AWS resource which provides information about the Gateway Device. Virtual Private Gateway is the VPN concentrator on and Amazon side of Site-to-Site VPN connection. These help you establish a VPN tunnel, which is an encrypted link to transmit data to and from the datacenter and AWS VPC. Every VPN connection includes 2 VPN tunnels for High Availability.
- Direct Connect: AWS Direct Connect enables you to securely connect the AWS environment to on-premise data center over a standard 1 gigabit or 10 Gigabit Ethernet fiber optic connection. This is dedicate, low latency connection which bypasses internet service providers in your network path.
VPC End Point
When you connect from EC2 instance to other AWS services like S3 or DynamoDB, the traffic is routed through the Internet. In many situations, this is unacceptable due to governance and compliance need. A VPC End Point enables private connections between your VPC and supported AWS services. VPC Endpoints services are powered by AWS PrivateLink. AWS PrivateLink is a technology that enables you to privately access services by using Private IP Addresses. The traffic between your VPC and the other services never leave Amazon network. A VPC endpoint does not require an Internet Gateway, Virtual Private Gateway, VPN Connection or NAT Devices. The instances in Private subnets can access the AWS services using VPC Endpoints, without the need to create NAT Gateways.